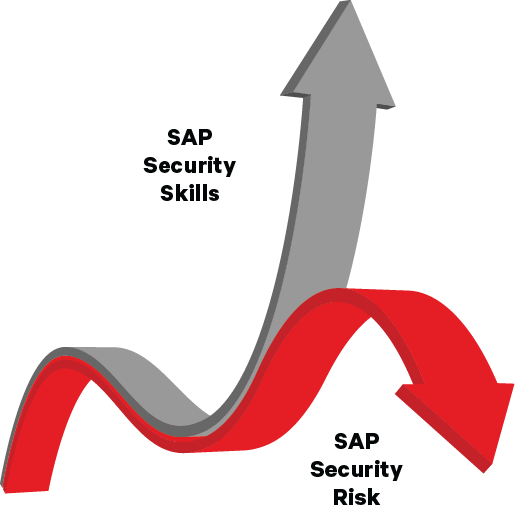
What Makes the Difference Between a Secure SAP Landscape and One at Risk of Cyberattack?
We believe PEOPLE hold the superhero powers that will ultimately keep proactive organizations cyber-resilient — now and in the future.
NO MONKEY Offers the Intel and Training You Need to Protect Your Crown Jewels
“We decided to conduct the Security Aptitude Assessment because we wanted to get transparency on our organization’s skills, knowledge, and responsibilities — especially among the different departments IT operations, security, and compliance. Carrying out this approach was very professional and helped us realize where we can improve our SAP Security area.”
Markus Weissensel, Chief Information Security Officer & Manager of Group IT at Fuchs Petrolub SE
NO MONKEY Empowers Teams To:
Turn Your Organization’s SAP Security Defenses into a Unified Army of Cyberdefenders
SAP landscapes (applications, operating systems, and databases) are highly complex and contain some of your most sensitive data. They require special knowledge and skills to protect.
Securing yours end-to-end requires the silo-free collaboration of 3 lines of defense, all unified around a dedicated SAP security strategy designed to reduce risk.
On top of that, SAP security requires human input. If your lines of defense don’t have the internal expertise to work together to take action, any optimization of processes, controls, and technology are just a ‘quick-fix’ for a symptom of the problem. To create a proactive SAP security culture that gets to the root of the problem, your people need to be up-skilled.
As experts in SAP security who have worked with clients around the world, we understand the challenges you’re facing.
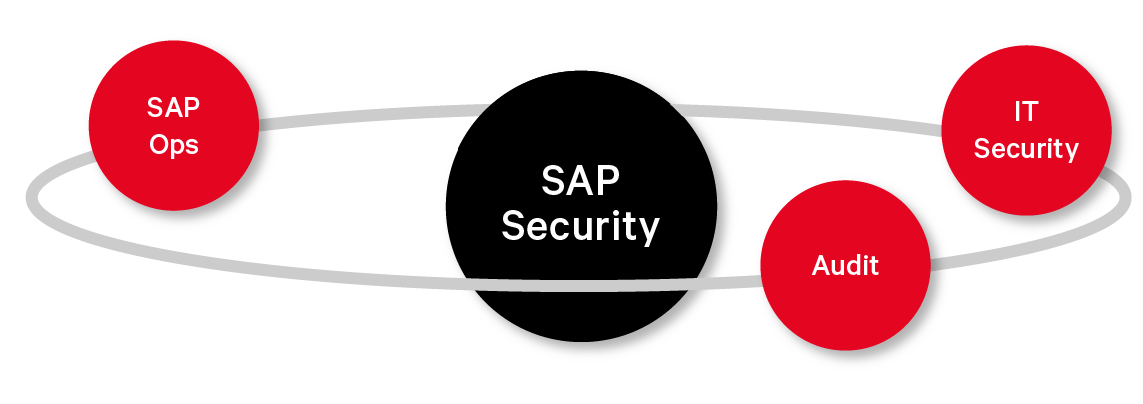
Unify Your SAP Security Defenses
- SAP Operations
- IT Security
- Audit
What Happens When Your SAP Security Defenses Exist in Silos?
When key stakeholders are not communicating, cyber risk drastically increases for business-critical SAP landscapes.
Siloed defenses cripple an organization’s internal ability to detect and respond. Teams focus all their energy on securing the front door and unknowingly leave the back door wide open to all kinds of threats and attacks.
NO MONKEY Live Online Training
Corporate SAP Security Training
Ready to improve your team’s SAP Security Posture? The quickest way for your people to attain the competencies needed to protect your SAP landscape is with our immersive, SAP security training bootcamp.
With a “learn-apply” approach, our Live Online Training offers interactive role-play, simulations, and assignments, together with a practice lab environment. Teaching from virtual classrooms, our expert trainers facilitate real-time discussions with and between learners.
The result? Participants gain a deeper understanding of SAP security – and can start practically applying it much sooner. Protecting SAP technology just got a whole lot easier!
NO MONKEY ADVISORY
Make Smart, Risk-based Decisions to Protect Your Business-Critical SAP Landscape
Your SAP landscape holds your most critical processes, and sensitive business data. Security vulnerabilities introduce immense risk to your customers and your bottom line.
You’re tasked with ensuring the continuity of business-critical operations while simultaneously protecting the digital assets of your organization and its customers. If you don’t have a clear understanding of your business risk and where your vulnerabilities lie, how can you make informed decisions about which protections and strategies you should put into place?
Improved SAP Security: What’s the Big Picture for the C-Suite?
As the CISO, you’re in the unique position to foster a security culture within your organization.
By empowering stakeholders with the important skills and resources, you can form a unified line of defense against cyberattacks. It’s up to you to take the reins and guide your organization’s SAP practices towards a continuously improving security posture.
Live Online Open Training Sessions
NO MONKEY ACADEMY Open Training Sessions offer a rotating schedule of the hottest role-based SAP security topics for SAP Operations, IT Security and Audit teams. They are great fit for smaller teams or individuals who want to learn with peers from other organizations.
Please note: Each open session is available based on capacity, and the maximum participants per session is limited to 14.
Browse through the NO MONKEY Open Training Sessions below and save your seat.
Stay Informed With the Latest From NO MONKEY
Subscribe to NO MONKEY updates to stay informed with the latest security tips, events, Open Trainings Session Calendar, Academy course offerings, Advisory services, and blog articles.
What Our Customers Are Saying
“Time flew by in this relaxed learning atmosphere; I would have wanted to have more.”
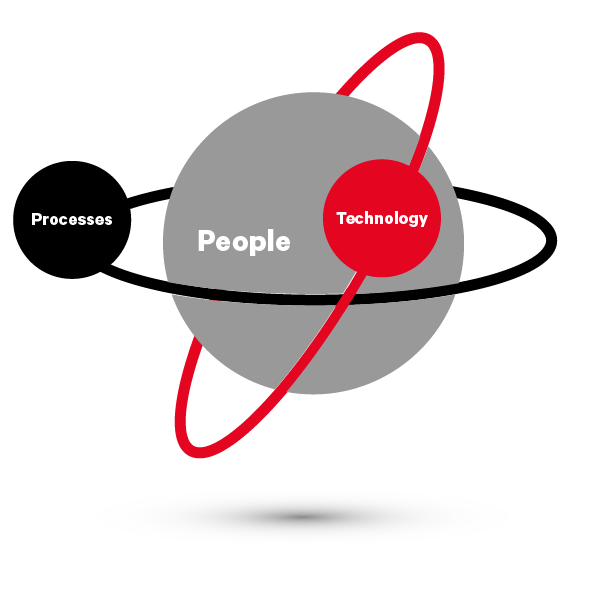
“SAP Security can be a minefield for the reactive organization. To reduce risk and safeguard our crown jewels, we have to think ‘end-to-end’ and be prepared to step outside the lines of boxed-in thinking. We practice a continuous, proactive approach to securing SAP applications based on processes, technology and people.”
“Safety is too serious for a subject to study without humor. Thank you for the entertaining training in NO MONKEY style!”
Memberships