For most organizations, the biggest hurdle to achieving SAP cybersecurity is a lack of visibility into their own operations.
Without a steadfast way to map security activities end-to-end, you can’t know where you’re vulnerable … until you’re the victim of a cyberattack, and it’s too late.
That’s a hard lesson to learn, and one you can’t truly afford.
But what if there were a tool that could grant you that insight? What if there were a way to map the operational areas of SAP against your core cybersecurity functions?
The NO MONKEY Security Matrix gives your business a way to protect critical SAP applications by aligning your cybersecurity activities with business requirements, risk tolerances, resources, and your overall security strategy.
The NO MONKEY Security Matrix Combines Cybersecurity Governance with Operational Cybersecurity
Using the NO MONKEY Security Matrix as a governance tool will give you a silo-free, comprehensive view of what goes into protecting an entire SAP landscape, giving you end-to-end insight into your SAP security, in line with industry-recognized frameworks.
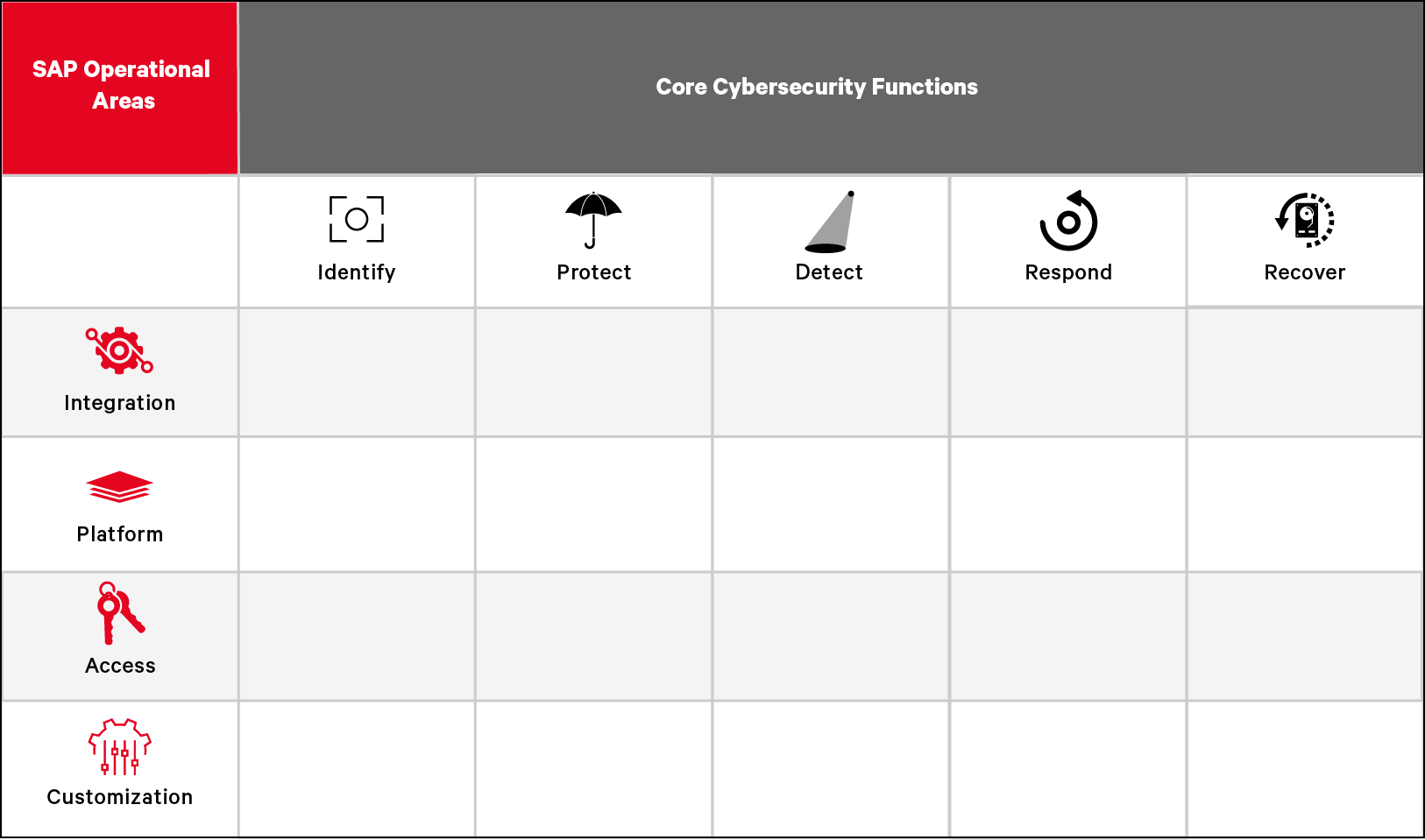
The Security Matrix is based on the National Institute of Standards (NIST) and Technology’s Cybersecurity Framework (CSF) core functions and adapted specifically for SAP operational areas. The combination of the two yields a powerful and holistic application of the CSF for SAP cybersecurity.
Here’s how they come together:
First, there are four main operational areas that need to be considered when securing SAP solutions end-to-end:

Integration – This area of SAP Operations focuses on the security of different integration scenarios within your SAP systems and for third-party tools integrating with your SAP environment.

Platform – Consideration of the vulnerabilities, hardening, and configuration of the SAP software.

Access – Consideration of access control and user authorizations measures and methodologies of SAP software.

Customization – Consideration of the customization of SAP software – including change management, custom code, business customizing, legacy interfaces, and add-ons.
Then, each of these SAP operational areas has five cybersecurity core functions that need to be considered to ensure protection:

Identify – Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.

Protect – Develop and implement appropriate safeguards to ensure delivery of critical services.

Detect – Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.

Respond – Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.

Recover – Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
The NO MONKEY Security Matrix
The NO MONKEY Security Matrix makes it straightforward for organizations of all sizes to apply the principles and best practices of risk management to proactively protect business critical SAP applications. Hover over the yellow dots below to see examples of how the matrix works.
How to Use the NO MONKEY Security Matrix
The Security Matrix can be used in three ways:

The NO MONKEY Security Matrix helps organizations, managers, C-levels, and team leads create a realistic strategy for security improvements and cybersecurity skills development.
The Security Matrix helps you:
- Continually apply SAP security best practices and key principles as you scale, regardless of your organization size
- Track improvements from your current security posture toward your maturity goals
- Increase transparency and determine accountability for stakeholders
- Determine overlaps and needs, helping you better evaluate managed security service providers
- Make informed buying decisions with a better understanding of how these tools will fit your security gaps
- Identify security standards and best practice frameworks for your SAP environment, while letting you map out and cross-reference your compliance frameworks
- Determine what’s needed to achieve desired certifications or implement best practices
The NO MONKEY Security Matrix provides a 360-degree, risk-informed approach to identifying, assessing, and managing SAP cybersecurity risk.
The Security Matrix helps you:
- Identify your unique cyber risks and critical gaps in your SAP defenses, from end to end
- Complement your SAP risk management and cybersecurity upskilling initiatives
- Illuminate ability and control gaps to make them visible to your C-suite and management team
While SAP security is critical to protecting your organization, it’s also one of the biggest skills gaps we see in cybersecurity. Using this tool helps you identify where those needs are and how to upskill your people. Your team members can also use the matrix to easily identify those training topics most relevant to their role and responsibilities.
Then, the NO MONKEY ACADEMY provides courses for all functions of the Security Matrix.
And as your people’s defenses get better and better, so does your SAP security. The NO MONKEY mindset will help them break down silos and work together to keep your organization safe.
The Security Matrix helps you:
- Identify your unique cyber risks and the critical skill gaps in your SAP defenses
- Complement your SAP risk management and cybersecurity upskilling initiatives
- Strengthen your cybersecurity up-skilling initiatives, by mapping out who carries out what activities to achieve the security objectives for a specific security function
- Manage educational efforts across teams and bring different departments and teams together to learn
- Map out individual learning paths based on work-role and responsibilities